GitFlow Adoption Strategy Integrated with DevSecOps
Executive Overview
This document defines the GitFlow branching strategy adoption plan and explains how it integrates with the previously defined DevSecOps security model.
The objective is to:
-
Standardize source control workflow across teams
-
Reduce merge conflicts and production instability
-
Improve release traceability
-
Align branching strategy with security controls
-
Embed security validation naturally into development flow
-
Build consistent engineering discipline
This is not just a branching strategy document.
It is a secure delivery governance model that connects GitFlow with automated DevSecOps enforcement.
Why GitFlow Matters in DevSecOps
DevSecOps is not only about security tools. It is about controlled, secure change management.
Without a structured branching model:
-
Security scans may be inconsistent.
-
Release tracking becomes difficult.
-
Hotfixes may bypass proper validation.
-
Production risk increases.
-
Audit traceability becomes weak.
GitFlow provides:
-
Clear lifecycle stages
-
Predictable MR patterns
-
Controlled promotion path
-
Separation of development vs release vs production
This structure perfectly aligns with the multi-stage DevSecOps pipeline.
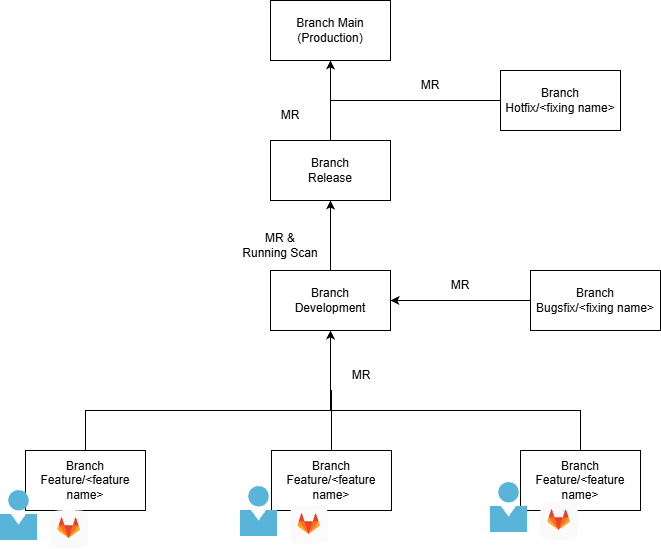
GitFlow Structure Overview
The GitFlow model consists of the following branches:
-
Main (Production)
-
Release
-
Development
-
Feature/<feature-name>
-
Bugfix/<fixing-name>
-
Hotfix/<fixing-name>
Each branch has a defined responsibility and corresponding security level.
Branch Roles and Security Integration
Main Branch (Production)
Purpose:
-
Represents production-ready code.
-
Always deployable.
-
Fully validated.
Security Requirements:
-
Must pass full DevSecOps pipeline:
-
Sonar Quality Gate
-
Dependency-Track policy
-
Harbor image scan
-
DAST validation
-
-
No direct commits allowed.
-
Only MR from Release or Hotfix allowed.
Governance Rules:
-
Protected branch.
-
Requires approval.
-
Requires pipeline success.
-
Signed commits recommended.
Production deployments are triggered only from this branch.
Release Branch
Purpose:
-
Stabilization branch before production.
-
Pre-production validation.
-
Final integration verification.
Flow:
Development → Release → Main
Security Enforcement:
-
Full SAST + SCA required.
-
Container image scanned.
-
Deploy to pre-prod cluster.
-
DAST executed.
No new features should be added.
Only stabilization fixes allowed.
Release branch acts as a security quarantine stage before production.
Development Branch
Purpose:
-
Integration branch for features and bugfixes.
-
Active development occurs here.
Flow:
Feature/Bugfix → Development
Security Activities at MR:
-
Sonar SAST (informational in early stage)
-
SBOM generation
-
Dependency-Track SCA
-
Credential scanning
At maturity:
-
MR blocked if quality gate fails.
Development branch ensures:
-
Security issues are identified early.
-
Code is aggregated safely before release.
Feature Branch
Naming Convention:
feature/<feature-name>
Purpose:
-
Isolated development for new functionality.
-
Created from Development branch.
Flow:
Feature → MR → Development
Security Integration:
-
SAST executed during MR.
-
SBOM generated.
-
SCA report posted to MR.
-
Developer responsible for fixing findings.
Policy:
-
Short-lived branch.
-
Frequent rebasing encouraged.
-
No direct push to Development.
Developer Habit Formation:
-
Developers must check:
-
Sonar dashboard
-
Dependency-Track report
-
MR security comment
-
This builds early security ownership.
Bugfix Branch
Naming Convention:
bugfix/<fixing-name>
Purpose:
-
Fix defects found in Development.
Flow:
Bugfix → MR → Development
Security Integration:
-
Same as feature branch.
-
Must not introduce new vulnerabilities.
-
Must maintain test coverage threshold.
Bugfix branches must pass DevSecOps scan before merge.
Hotfix Branch
Naming Convention:
hotfix/<fixing-name>
Purpose:
-
Urgent production fix.
-
Created from Main branch.
Flow:
Hotfix → MR → Main
Security Integration:
-
Accelerated but not bypassed.
-
SAST + SCA still executed.
-
Container scan mandatory.
-
DAST may be targeted or reduced scope (based on urgency policy).
Governance:
-
Requires higher approval.
-
Must merge back into Development after production deployment.
This prevents production drift.
Integrating GitFlow with DevSecOps Pipeline
Below describes how security layers align with branch lifecycle.
Feature → Development Stage
Security Focus:
Shift-Left.
Tools:
-
Sonar (SAST, credential scan, unit test policy)
-
Trivy SBOM
-
Dependency-Track SCA
Goal:
Catch vulnerabilities early.
Enforcement Strategy:
-
Early phase: Informational.
-
Mature phase: Hard Quality Gate.
Development → Release Stage
Security Focus:
Integration integrity.
Tools:
-
Full SAST
-
SCA policy check
-
Container scan
-
Deploy to Pre-Prod
-
DAST scan
Goal:
Ensure system-level stability.
Release → Main Stage
Security Focus:
Production safety.
Requirements:
-
All gates passed.
-
No Critical vulnerabilities.
-
Coverage threshold met.
-
DAST passed.
-
Approval granted.
Developer Habit Formation Strategy
This is the most critical section.
We do NOT enforce blocking immediately.
Instead, we implement:
Phase 1 – Awareness
-
Developers required to check MR security comments.
-
Security review part of code review checklist.
-
Weekly vulnerability review.
-
Security dashboards visible to team.
No blocking yet.
Phase 2 – Guided Enforcement
-
Warn if thresholds exceeded.
-
Highlight top risky repos.
-
Share metrics per team.
Developers begin self-correcting.
Phase 3 – Hard Enforcement
Now enable:
-
Sonar Quality Gate blocking MR.
-
Dependency-Track policy enforcement.
-
Harbor vulnerability threshold enforcement.
-
DAST blocking production.
By this time:
-
False positives minimized.
-
Developers trained.
-
Trust established.
Governance & Policy Rules
Branch Protection Rules
Main:
-
Protected
-
No direct push
-
Approval required
-
CI must pass
Release:
-
Protected
-
Approval required
-
CI must pass
Development:
-
MR required
-
No direct push
Naming Convention Enforcement
feature/*
bugfix/*
hotfix/*
release/*
Automated branch validation recommended.
Security Responsibilities per Branch
| Branch | Security Level | Enforcement |
|---|---|---|
| Feature | Early detection | Soft |
| Bugfix | Early detection | Soft |
| Development | Aggregated validation | Medium |
| Release | Pre-prod validation | High |
| Main | Production safe | Strict |
Comparison with Ad-Hoc Branching
| Aspect | Ad-Hoc | GitFlow Integrated |
|---|---|---|
| Release control | Weak | Structured |
| Security integration | Inconsistent | Aligned |
| Production stability | Risky | Controlled |
| Audit traceability | Limited | Strong |
| Hotfix governance | Chaotic | Managed |
Final Conclusion
Adopting GitFlow is not merely a version control decision.
It is a security and governance decision.
When integrated with DevSecOps:
-
Every branch represents a security maturity stage.
-
Every promotion step represents a security validation checkpoint.
-
Production becomes the result of layered verification.
The organization transitions from:
Reactive security→Controlled secure software lifecycle
This creates:
-
Predictable delivery
-
Secure release cycles
-
Developer accountability
-
Sustainable DevSecOps culture